NFC Tag Programming Service
Duolabs has developed entirely in-house both the hardware and software dedicated to programming NFC Tags (see the tag types). This proprietary infrastructure lets us manage all encoding phases securely and flexibly—from writing the information to verifying correct programming—ensuring full reliability and traceability.
A distinctive service offered by Duolabs is NFC Tag serialization, performed according to the customer’s custom algorithm. Serialization can be based on the serial number (UID) and implemented using symmetric cryptography such as AES and 3DES, asymmetric algorithms such as RSA and ECC, as well as hash functions like SHA. This flexibility guarantees a wide range of secure solutions adaptable to every customer need.
To meet industrial production requirements, Duolabs has refined its technology to handle tags on rolls with variable spacing up to 4 millimeters, eliminating anticollision issues. Thanks to this, it’s possible to program up to 32 Tags per system simultaneously. The systems themselves are designed to be scalable and replicable, enabling the creation of many parallel production lines and ensuring very high output capacity.
The programming process ensures not only correct data writing but also the verification of each individual Tag. All UIDs are recorded to guarantee complete traceability: every Tag is linked to the original roll, the machine that programmed it, and even the specific reader that verified its functionality. This level of detail allows total supply-chain control and ensures certified quality. In addition, defective Tags (BAD) are removed and replaced, guaranteeing rolls that are 100% working.
Duolabs’ production capacity ranges from 50,000 to 500,000 Tags programmed per day, depending on the type of serialization required and the complexity of the information to be written. This scalability allows us to respond promptly and reliably to both small projects and large industrial supply volumes.
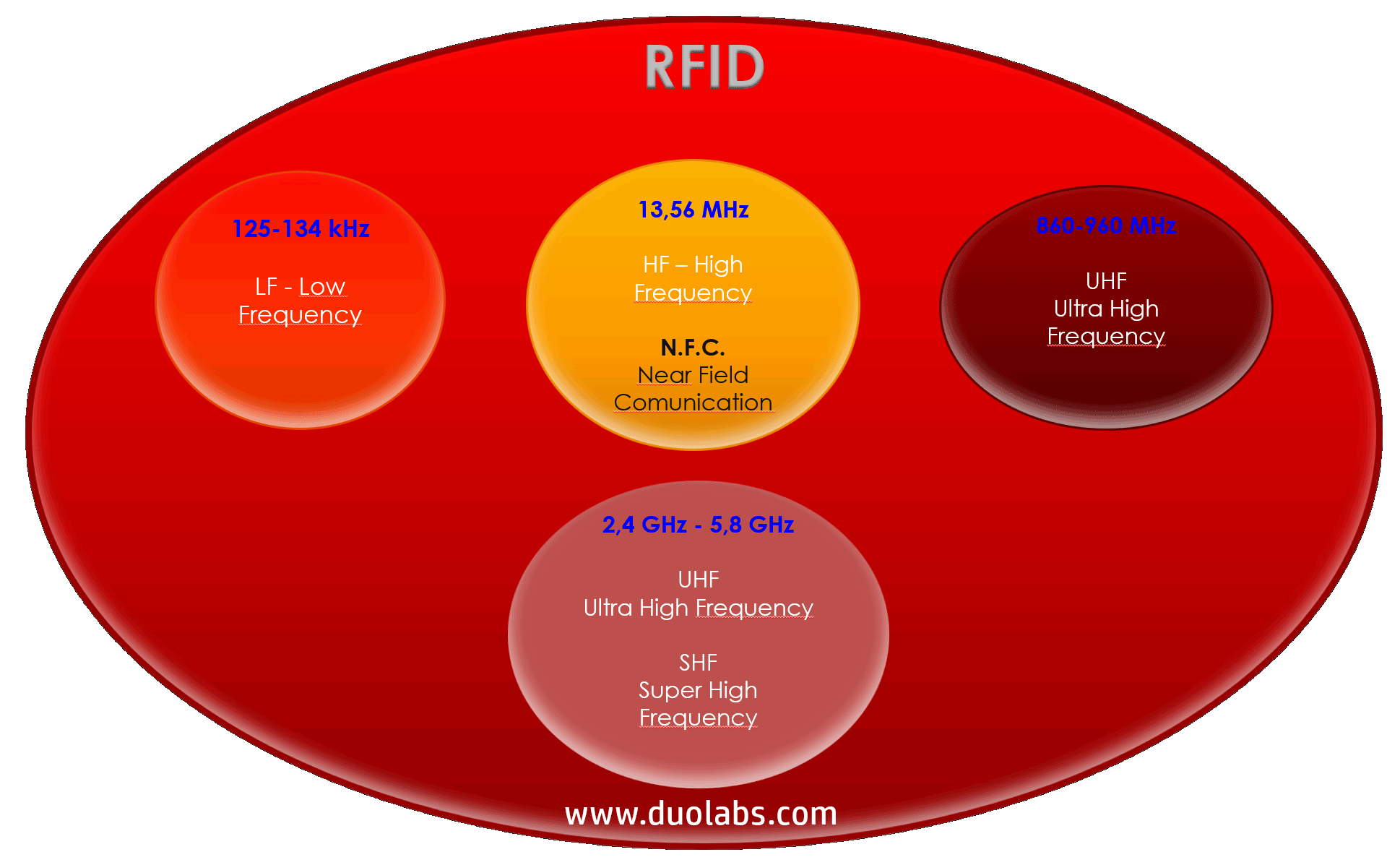
The hardware and software developed by Duolabs are completely proprietary and were created to ensure maximum compatibility and customization. This makes it possible not only to program all standard Tags, but also advanced devices such as NTag, which offer special features for complex, next-generation applications. We support the ISO 14443, ISO 15693, and ISO 18000 standards, ensuring global compatibility.
Thanks to our long-standing experience in the DVB sector, where piracy issues required extremely secure systems, Duolabs provides advanced expertise for building secure encoding solutions. This know-how is transferred into NFC projects to ensure protection, effectiveness, and resistance to fraudulent attacks.
Besides programming, Duolabs offers fine-tuning services for NFC readers, including antenna calibration and the design of customized RFID readers, together with the software to manage them. This integrated approach enables complete, optimized systems for every application scenario.
To address issues related to unauthorized production or handling extra lots, Duolabs provides a cloud platform for remote generation of NFC Tag payloads. This solution ensures traceability, certified origin, and data security, allowing complete control of the production chain.
Duolabs has also developed innovative systems for consumable protection such as DuoLocker, designed to guarantee the authenticity of consumable materials and prevent the use of counterfeit components.
Finally, the company offers years of experience in digital security for creating systems that allow verification of the authenticity of final products. This expertise ensures robust, reliable solutions to protect your business.
In addition to programming services, Duolabs also handles direct sourcing of Tags from certified suppliers, offering a turnkey service from material supply to customized serialization.